COVID-19 and Cybersecurity
What you need to know today and how we can create resilient cybersecurity for tomorrow
Covid19 has created new revelations about the dearth of cybersecurity within many video conferencing tools. This isn’t news to cybersecurity professionals who have been concerned about these vulnerabilities for years.
I am a cryptographer by training. My graduate work at Johns Hopkins was incorporated into the encryption protocols in apps like Whatsapp and Signal. I work on the Google security team and collaborate on cyber security across the Silicon Valley. I’m very familiar with the fact that deprioritizing privacy is tempting for resource constrained product managers and inviting for hackers.
Cybersecurity is on our all minds now that we must work from home for the foreseeable future. Previously confidential conversations will all be happening over the internet - an exciting opportunity for intelligence agencies and hackers alike if we are not careful.
But how can we know which products to trust? Looking back, why do we continue to rely on products that essentially ignore the privacy needs of users until a crisis hits? Zoom may be on the receiving end of public pressure in COVID 19, but the cycle of ignoring privacy at the expense of other features is an old story.
This blog post:
- Breaks down the subcomponents of cybersecurity and usability, using this framework to rank the most popular messaging tools out here
- Using this data, I recommend platforms for personal and business use (Hint: use WhatsApp and Skype)
- For those that must Zoom, I set out some actionable steps that can be taken to reduce risk.
- I review how we ended up here (again), identifying perennial disincentives to invest in cybersecurity that have produced a scenario where the market leaders are providing substandard security to users.
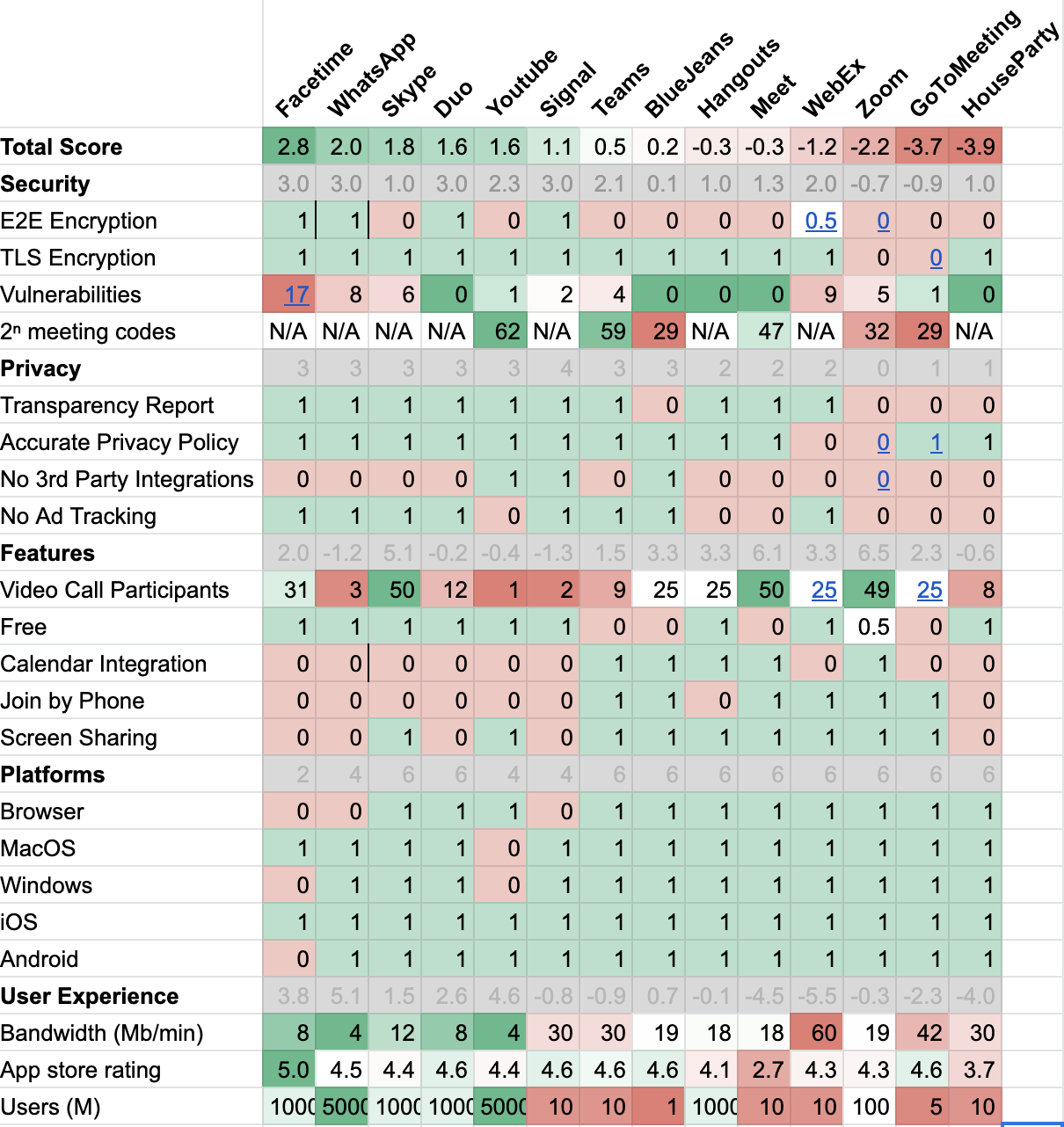
A Data Based Comparison of Video Chat Apps
Cybersecurity is referred to as a single input, but we all know it is made up of many features. I break down the most important features and use them to rank popular apps:
Security
- End to End Encryption protects the confidentiality of your meeting, even from the company hosting the product. This is the highest level of security available.
- TLS Encryption is the same kind of security that most websites use. A failure to use even the most basic form of encryption represents a significant lack of investment in product safety.
- Vulnerabilities lists the total number of standardized security failures that a product has had. This number often correlates with product complexity, longevity, and scrutiny.
- 2ⁿ meeting codes ranks the probability zoom bombing, which becomes trivial when more than 2^(n/2) calls are in progress due to math quirk known as the birthday problem.
Privacy
- Transparency Report Does the company publicly disclose its relationships and cooperation with governments around the world?
- Accurate Privacy Policy Does the company have deceptive or demonstrably false language in its products and or privacy policy?
- No 3rd Party Integrations Does the product send your personal data to other companies such as Facebook, Google, or LinkedIn?
User Experience
- Minimum Bandwidth required to make a video call. This is a proxy for how well the app performs under low bandwidth conditions.
- Number of Users is a proxy for how likely the person you are trying to call already has, and understands how to use this app.
Recommendations
It should be apparent now that there isn’t one clear winner when we look at the many features that together make a product secure and usable. The data still points to some front runners when we think about which products to rely on.
For Personal Use
- FaceTime
- Google Duo
All three offer excellent security, respectful privacy policies, a broad user base, and even work well when the internet is slow. Why settle for a worse experience and worse privacy if you don’t need screen sharing or calendar integration?
For Business Use
- Skype
- Google Hangouts
- BlueJeans
These three offer respectful privacy policies, high numbers of simultaneous video participants, and screen sharing.
If you can’t help but use Zoom
Zoom’s shockingly poor security has been well documented. A recent surge in use has surfaced long standing vulnerabilities, not least the potential for “zoombombing.“
But what can you do to take care of your own privacy and security if someone adds you to a call?
- Don’t be tricked by the lock icon. It means nothing. Your call can be easily eavesdropped on, which might be fine, but you should be aware.
- Don’t share meeting links in public websites or large groups. This encourages uninvited guests.
- Uninstall the application. You don’t need it and it only makes you more hackable.
- Turn on Waiting Rooms. This allows the host to vet guests as they arrive.
- Use a random and gathering-specific meeting ID. Your personal ID doesn’t change from meeting to meeting, inviting anyone from prior meetings to crash in the future.
- Use host privileges effectively. Turn off screen sharing. Turn off screen drawing.Turn off file transfer.
Can we use the same apps for work and play?
Probably not. Enterprise environments often need features that are incompatible with the needs of at-home users. For example:
- Office video conference products don’t work as well over home internet, especially when the whole world is online at the same time.
- Office features such as dialing in over the phone and meeting codes by definition lack end to end encryption and are de facto less secure.
Learning from the COVID19 Cybersecurity Crisis
The Privacy vs. Features Paradox
It is not a mistake that the products with the most features offer the least amount of privacy. Engineering resources are finite and time spent building security is time lost developing features that promote user adoption and business growth.
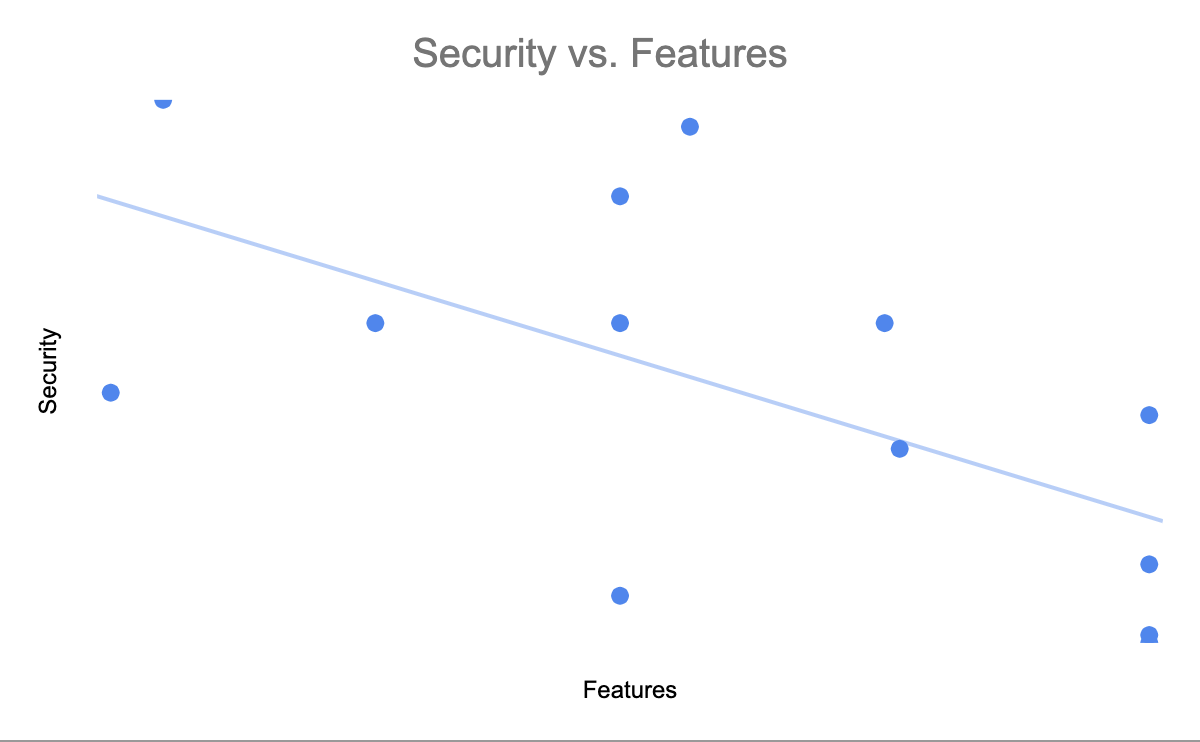
This is a pernicious incentive structure where features get rolled out quickly to promote business growth, while the hidden costs of under investing in safety puts users at risk without their knowledge. Users don’t understand or prioritize security which disincentivizes companies from prioritizing online safety. It is only when disaster strikes that companies make the privacy investments we deserved from the start.
Market Failure for User Safety
Users deserve a minimum standard of digital safety from all products in the marketplace, even fledgling startups without the resources to hire privacy engineers. COVID 19 has highlighted this gap.
In a world of work from home, it is clear that users deserve some form of third party verification that goes beyond asking lay users to individually assess the highly technical safety components of evolving products. Let’s not forget that regulatory bodies vet and certify other safety critical components of our lives from health technology to electricity before these technologies go to market.
Why does our online life lack these protections?
A Cyber Underwriters Laboratory that vouches for the digital safety of products could have independently certified the security of popular products and made up for some of the missing incentives that have landed us in this mess in the first place.